CCleaner malware specifically targeted Microsoft and other tech firms
The recent CCleaner malware attack specifically went after tech firms, including Microsoft, according to new analysis.
Though it seemed like a more general malware outbreak at first, the recent CCleaner debacle appears to have been more targeted than originally thought. Since it was revealed CCleaner developer Piriform had unknowingly been distributing malicious software with the utility for a month, researchers have discovered that the malware was specifically trying to gain access to internal networks in at least 20 tech companies, including Microsoft.
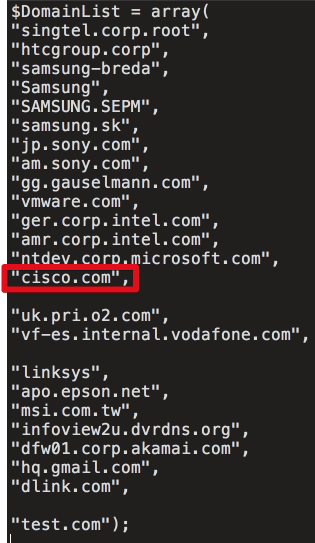
First reported by Wired (via The Verge), researchers at Cisco and Avast discovered that the malware was specifically going after a list of internal domains at the time its "command-and-control" server was seized. Targeted companies include Intel, Google, Microsoft, Akamai, Samsung, Sony, VMware, HTC, Linksys, D-Link and Cisco, among others, as part of a two-stage attack. Avast writes:
At the time the server was taken down, the attack was targeting select large technology and telecommunication companies in Japan, Taiwan, UK, Germany and the US. Given that CCleaner is a consumer-oriented product, this was a typical watering hole attack where the vast majority of users were uninteresting for the attacker, but select ones were.
According to Cisco, the hackers appear to have been successful in installing the malware on more than 700,000 machines,"and more than 20 machines have received the second-stage payload." That's only for a four-day period between September 12 and September 16, so it's possible that other companies were targeted.
The attack still hasn't been attributed to any specific party, but evidence suggests it could be part of an industrial espionage campaign. A Kaspersky researcher has indicated the malware shares code with tools used by Axiom, a group that has been linked to Chinese intelligence services.
Get the Windows Central Newsletter
All the latest news, reviews, and guides for Windows and Xbox diehards.
Dan Thorp-Lancaster is the former Editor-in-Chief of Windows Central. He began working with Windows Central, Android Central, and iMore as a news writer in 2014 and is obsessed with tech of all sorts. You can follow Dan on Twitter @DthorpL and Instagram @heyitsdtl.

